Consciousness for General Concerns of Information Security
The scope of information security is much broader than just encrypting information. Even broader than the entire field of cryptology.
The following graphic is intended to provide an overview of the subject areas of information security in order to give you an awareness of general information security concerns.
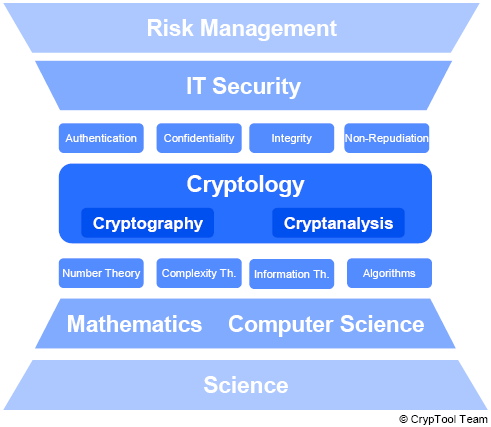
IT security describes comprehensive activities which suport the operation of IT systems with security measures, to provide safeguard for the electronic data of companies as well as their clients and vendors. The aim is to protect information and processes as well as exclude IT related adverse effects of business activities as far as possible.
The measures of IT security include (besides cryptology methods) e.g. security organisation, legal aspects, security monitoring, anti virus measures, patch management, disaster recovery, business continuity, security architectures and awareness for IT security. A good overview of these measures can be found at NIST or at the German information security agency (BSI).
Risk management extents the scope of IT security and also covers the socially desirable protection of critical infrastructures.
Risk management can be defined as the consciously management of risks. This can include general operational risks or specific financial risks. Companies, organisations and individuals must deal with all sorts of risks within living memory. The origin of a systematic risk management is based in the financial industry. Today several laws contribute and aim to provide financial control and transparency for corporations (e.g. Sarbanes-Oxley Act, or Basel II).
The total risk of a company can be divided into operational risks (e.g. breakdown or limitations of IT systems) or all sorts of financial risks (credit risks, liquidity risks, market risks, liability risks etc.).
Several approaches exist to identify, measure, monitor and control risks.
Risk management does not necessarily aim at complete risk prevention. Instead it tries to identify appropriate actions under a cost and benefit perspective (appropriate measures could also include the insurance of certain risks).
A basic understanding of cryptology is necessary to take appropriate measures and controls in order to achieve the objectives of IT security (authentication, confidentiality, integrity, non-repudiation) with an optimal cost-value ratio. The following figure illustrates how Cryptool can contribute to the understanding of security awareness in this context:
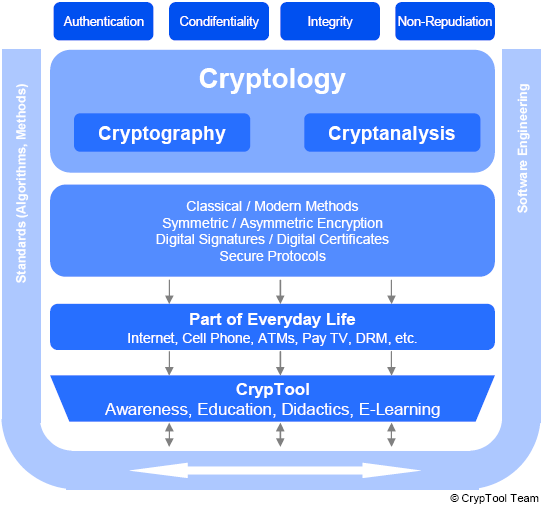
Standardisation and Management Visibility of Cryptology
Besides the previous classifications originated from a technical and risk management perspective, key areas of cryptology can be structured in the 5 components: algorithms, protocols, key management, organisational best practice and regulatory requirements. These main components are characterised by very different positions in terms of grade of standardisation, corporate/management visibility and scientific focus.
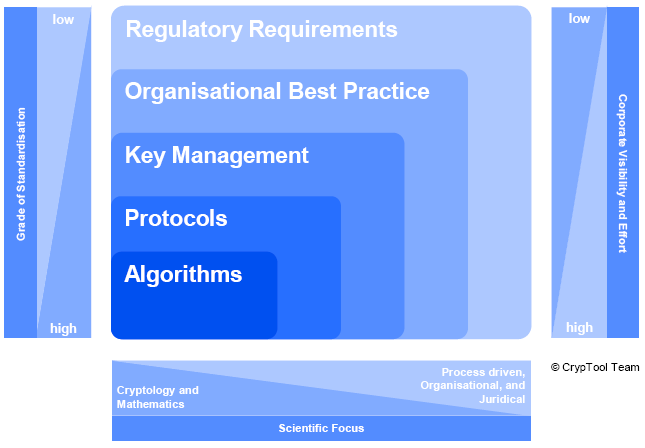
Algorithms
Algorithms and related mathematic functions are the foundation of cryptology. Algorithms such as AES, 3DES or RSA are highly standardised and are subject of cryptology and related mathematics research.
Protocols
Protocols use algorithms. They are used to protect data transfer between communication partners and are therefore the inevitable enabler of the commercial use of electronic communication. Typical security protocols include TLS, SSL or IPsec. These protocols are also highly standardised and are well known by many users because of their widespread implementation in intranet and internet communication.
Key Management
An important part of cryptology is the management of encryption and decryption keys, the so called key management. Because most algorithms and protocols are based on keys, key management and storage is essential. A number of standards exist in the area of key managements such as ISO, PKIX or XKMS.
Best Practice Implementation
A fundamental aspect, especially from a corporate perspective is the implementation of cryptology, both organisational and technically. Derived from risk management, appropriate mechanisms of IT security have to be implemented, which often results in the implementation of cryptology methods. In this context cryptology has to be often implemented in heterogeneous IT landscapes and to protect information processed with frequently changing technologies.
Regulatory Requirements
Regulatory requirements are set by the legislator and the corporations have to meet these requirements as they are required by law. With regards to the area of cryptology it is important to establish common standards in order to protect electronic data exchange. Additionally legal certainty, meaning the predictability of legal decisions is necessary to lawfully safeguard electronic communication secured by cryptology (e.g. digital signatures).
CrypTool in Education
Humanity has concerned itself with the topic of cryptology for three thousand years. However, until the mid-20th century it was a topic of importance to only a small interested group – diplomats and the armed forces. In any military conflict, exchange of confidential information and eavesdropping is crucial for survival. Due to the sensitive subject matter the vast majority of crypto research was done in secrecy in the past.
With the advent of the information age and the introduction of the internet for public use, new scenarios for cryptographic techniques became available, e.g.:
- Encrypted connections and secure authentication for online banking
- Encrypted communication in mobile phone networks
- Encrypted and binding communication via e-mail
- Electronic alternatives for a handwritten signature
- Electronic protection of (intellectual) property (DVD, Pay-TV)
- Car-theft protection systems (immobiliser)
Even though the above listing of non-military, commercially driven applications is incomplete, it demonstrates that today cryptology affects every member of the information society. Thus, research and teaching in the field of cryptology are of great importance.
At first the crypto research in the commercial sector has been performed with the public excluded. As a consequence of unpleasant experiences with the Security by Obscurity approach, companies gradually adopted the so-called Kerckhoffs' principle, which was already formulated in 1883.
The security of a cryptographic system must not depend on the secrecy of the algorithm. The security is only predicated on the secrecy of the key.
Meanwhile, by adhering to this principle, public research and teaching in the field of cryptology has become well-known and will be of even greater importance in the future. CrypTool provides an ideal environment for the learning of cryptologic history and the current state of crypto research and its applications. The CrypTool program and additional material can be used for self-study and in lectures.
Ideas for every-day security
On this page, we present ideas that you can use to increase your safety in everyday life.
2021
-
Steve Vaillancourt, practicum report, Solving the Problem of Password-Based User Authentication
More details
This report documents the demonstration of an authenticator application that uses public key encryption to secure access to web applications. Passwords are replaced with digital signatures to initiate authenticated sessions. The authenticator generates and manages private/public keys for the user, and only the public keys need to be shared with the web server. The authentication scheme uses a custom authentication protocol to partially automate the process and alleviate user effort. A new idea is to use the drag&drop functionality of the browsers for entering authentication data. A complete risk analysis based on the Mitre Att&ck Knowledge Base is included in the report.
